

A PRISMAsync Print Server printer can act in a Local Area Network (LAN) protected by IEEE 802.1X. The 802.1X standard provides the possibility to accept or to deny a network connection based on the identity of a endpoint. This endpoint can be a user, a device or an application. As long as the endpoint has not been identified and verified, the access to other endpoints of the protected network is not possible.
IEEE 802.1X security is based on the status of the Local Area Network (LAN) ports of the clients. An IEEE 802.1X configurable Local Area Network (LAN) port can be dynamically enabled or disabled. The results of theIEEE 802.1X authentication process determine if the port will be enabled or not.
Framed text in this topic describes the IEEE 802.1X implementation of PRISMAsync Print Server.
The IEEE 802.1X standard distinguishes the following components: supplicant, authenticator and authentication server.
Supplicant
The client, for example PRISMAsync Print Server, that requests access to the Local Area Network (LAN) and responds to requests from the authenticator.
Authenticator
The authenticator is a switch or router that controls the physical access to the network. The access is based on the authentication status of the client. The authentication is performed by the authentication server. The authentication server is the RADIUS (Remote Authentication Dial-In User Service) server in Windows Server.
Authentication server
The authentication server verifies the identity of the supplicant. The industry standard of the authentication server is a RADIUS server. The Network Policy Server (NPS) is a service included in Windows Server. Its acts as RADIUS server to authenticate clients against Active Directory. The RADIUS server informs the authenticator that the client is authorised to access the local area network.
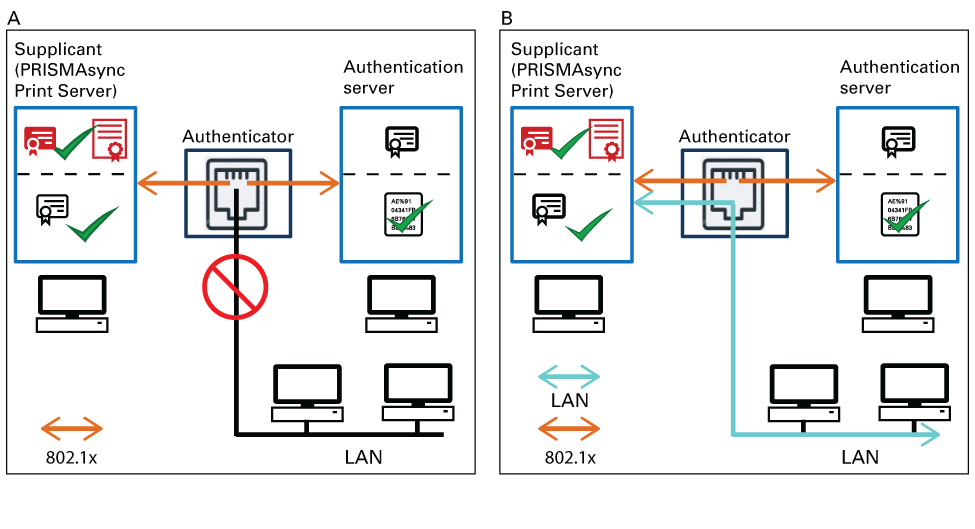 IEEE 802.1X components and their tasks
IEEE 802.1X components and their tasksThe scheme is a simple overview of how IEEE 802.1X works.
A. Before the port authentication, the identity of the supplicant, for example PRISMAsync Print Server, is unknown and all data traffic to the protected side of the network is blocked. The IEEE 802.1X communication enables the exchange of identity information, such as identity certificates and enables negotiating of the used protocols and authentication methods.
B. After the port authentication, the traffic to the protected side of the network is possible.
|
PRISMAsync Print Server uses Windows 10 client to act as supplicant and supports Windows Server 2016 as authentication server (RADIUS server). |
In general, IEEE 802.1X uses Extensible Authentication Protocol (EAP) to negotiate the authentication method of the supplicant and the authentication server. The supplicant can use a certificate, a smart card, or credentials to identify.
EAP collaborates with additional authentication protocols, such as Transport Layer Security (TLS) and Microsoft Challenge Handshake Authentication Protocol version 2 (MS-CHAP-V2).
EAP-TLS
EAP-TLS is used in certificate-based security environments. It provides the strongest authentication and key determination method. EAP-TLS requires that the supplicant has an identity certificate.
EAP-MS-CHAP-V2
EAP-MS-CHAP-V2 is a mutual authentication method that supports password-based endpoint authentication.
Not all authentication servers, supplicants and LDAP directory servers support all authentication methods.
|
PRISMAsync Print Server supports: EAP-TLS and EAP-MS-CHAP-V2. |
Protected EAP (PEAP) is a protocol that increases the security of EAP-TLS and EAP-MS-CHAP-V2.
PEAP builds an encrypted channel during the second part of the EAP negotiation process. Inside this secure channel a new EAP negotiation takes place in order to authenticate the supplicant.
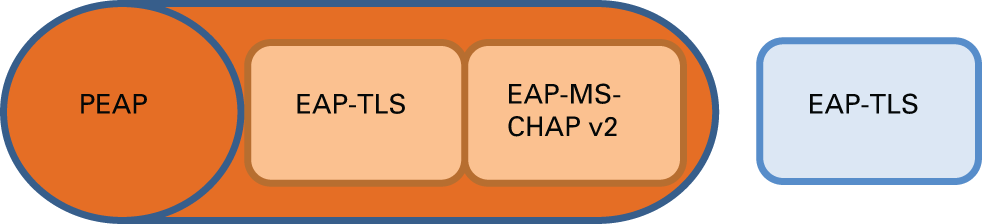 PEAP
PEAPPEAP with EAP-TLS
PEAP with EAP-TLS provides the highest level of security by protecting the Identity certificate of the supplicant during the transfer to the authentication server.
PEAP with EAP-MS-CHAP-V2
PEAP combines the easy to configure EAP-MS-CHAP-V2 with an extra security level by encrypting the EAP-MS-CHAP-V2 credentials. PEAP with EAP-MS-CHAP-V2 is generally used in Microsoft Active Directory environments.
|
PRISMAsync Print Server supports the following authentication methods: PEAP with EAP-TLS, PEAP with EAP-MS-CHAP-V2, and EAP-TLS. |
All authentication methods require that the trusted CA certificates of the authentication server are available on the supplicant.
EAP-TLS requires a valid Identity certificate of the supplicant that is mapped to a user account or computer account in the LDAP directory server (Active Directory Domain Services (AD DS)).
When the Identity certificate refers to a computer, the Subject Alternative Name (SubjectAltName) field in the certificate must contain the Fully Qualified Domain Name (FQDN) of the client.
When the Identity certificate refers to a user, the Subject Alternative Name (SubjectAltName) field in the certificate must contain the User Principal Name (UPN).
EAP-MS-CHAP-V2 does not use an Identity certificate of the supplicant.
EAP-MS-CHAP-V2 requires an MS-CHAP-V2 username and a MS-CHAP-V2 password that you configure in the Settings Editor. |
An IEEE 802.1X authentication can be initiated by either the authenticator (the switch) or the supplicant. When the authenticator detects a link up to the port, it sends a message to the supplicant.
It is usually not needed to re-authenticate a previously authenticated endpoint that remains connected to the network. After a successful IEEE 802.1X authentication, the port remains open until the connection is terminated, for example when the physical link shows a down status. As long as the physical link is maintained, the authenticated endpoint remains connected to the port.