

Internet Protocol security (IPsec) is a suite of related protocols to set up secure communications at the IP packet level. The hosts that want to establish an IPsec connection uses specific negotiation methods. Hosts negotiate about the key exchange, encryption algorithms and the authentication method.
PRISMAsync Print Server can use IPsec for host authentication, data authentication and data encryption. For host-to-host communication, PRISMAsync Print Server provides IPsec options to configure scalable access to network locations that are considered as trusted.
This topic describes the main components of IPsec. Framed text describes the IPsec implementation of PRISMAsync Print Server.
TCP/IP protocols can be mapped into a four-layer conceptual model known as the DARPA model. The four layers are: Application, Transport, Internet, Network. The layers of the DARPA model corresponds with one or more layers of the Open Systems Interconnection (OSI) model. IPsec is integrated in the Internet layer, where it provides security for many protocols of the Application layer.
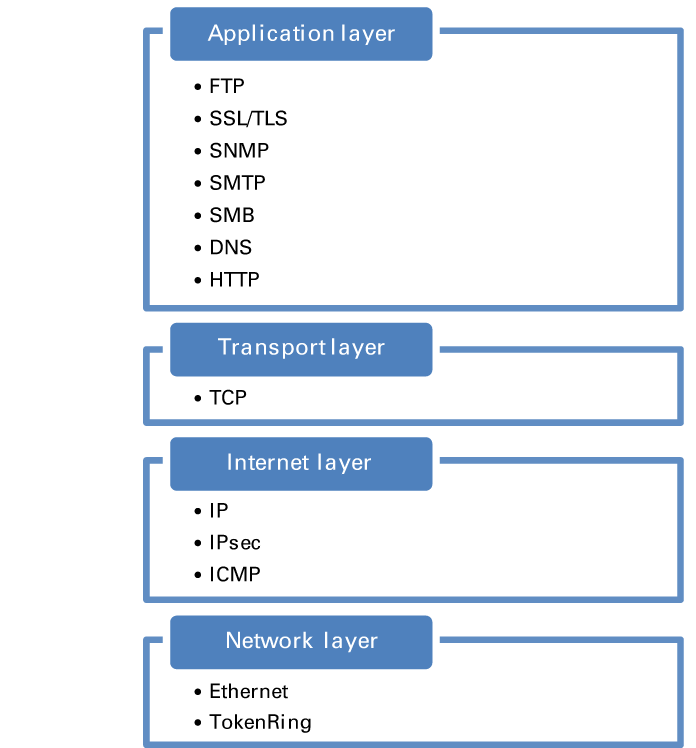 Open Systems Interconnection (OSI) model
Open Systems Interconnection (OSI) modelHost authentication can occur via a pre-shared key or via certificate-based authentication.
The pre-shared key needs to be created and stored at both sides before an IPsec session starts.
Certificate-based authentication is a mutual process. Both hosts need to send their Identity certificate.
|
PRISMAsync Print Server supports the use of pre-shared keys and certificate-based authentication. PRISMAsync Print Server accepts the following signing algorithms: ECDSA 256, ECDSA 384, RSA. Certificate-based authentication can be combined with pre-shared key authentication. If the certificate-based authentication is not successful, the pre-shared key is used. You select the host authentication method in a PRISMAsync Print Server IPsec rule. |
Diffie-Hellman (DH) exchange enables two hosts to calculate the same secret key without sending secret values over a public link. The shared key encrypts all following communication.
As part of the negotiation, the hosts must agree on the Diffie-Hellman group. A Diffie-Hellman group determines the strength of the shared key. Higher Diffie-Hellman group numbers are more secure, but need more additional resources to calculate the key.
|
PRISMAsync Print Server uses Diffie-Hellman for key cryptography. PRISMAsync supports: DH Group 14, DH Group 24, Elliptic-curve Diffie–Hellman (ECDH) P-256, ECDH P-384. |
IPsec can use two security protocols:
Authentication Header (AH), that contains algorithms to authenticate the source of an IP packet (data origin authentication) and to verify the content integrity (data authentication).
Encapsulating Security Payload (ESP), that contains algorithms to ensure the privacy (encryption) and content integrity (data authentication).
|
PRISMAsync Print Server only uses Encapsulating Security Payload (ESP). |
ESP encrypts the IP packet data (payload) and not the IP address of the destination. ESP encapsulates the original IP payload with an ESP header and trailer. Each IPsec data packet has a unique SA index (SAI) that refers to the Security Association (SA) that has been agreed on. The receiver uses the SA index to find the SA that belongs to this IP packet. Both hosts use the same key to encrypt and decrypt the IP payload.
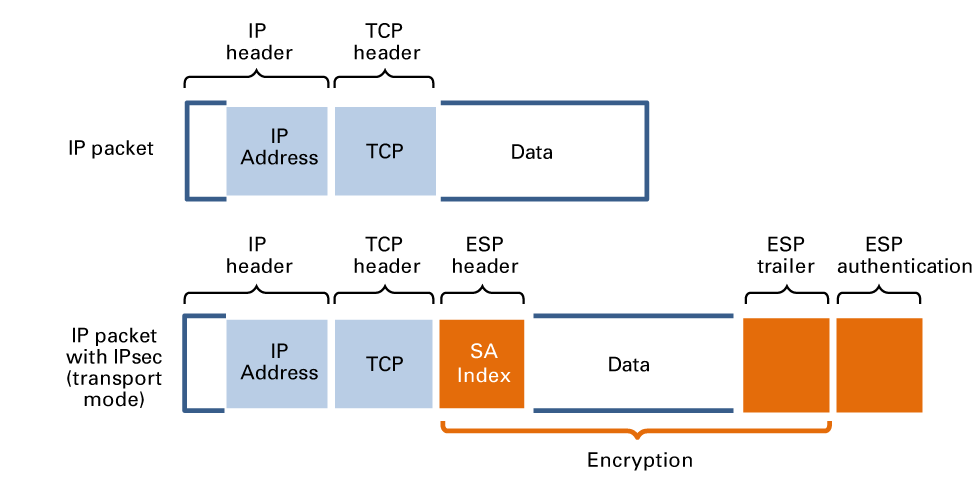 IP packets without and with ESP encryption
IP packets without and with ESP encryptionIPsec can run in two modes to encrypt the IP packet: transport mode and tunnel mode. In transport mode only the IP payload is encrypted. The tunnel mode is typically used for VPN where a tunnel is established over the Internet and where the entire IP packet will be encrypted.
|
PRISMAsync Print Server only uses transport mode. |
Network address translation (NAT) is a method to modify IP address information of IP packets during the transfer. When the IP address information has been changed by NAT, the SA does not contain the correct reference to the IP address of the destination. IPsec will discard the IP packets as a result.
Network Address Translation-Traversal (NAT-T) can detect if there are one or more NAT devices on the link. In that case NAT-T encapsulates the IP data packet with an extra layer so that the address translation will not lead to loss of data packets.
|
With PRISMAsync Print Server you can enable NAT-T in two ways: Use NAT-T when the remote endpoints are behind a NAT device. Or, use NAT-T when both endpoints are behind a NAT device. |
The distribution and management of secret keys are important to use IPsec successfully. IPsec uses the Internet Key Exchange (IKE) protocol to negotiate about the use of keys and to automatically generate secret keys.
|
PRISMAsync Print Server uses the Internet Key Exchange (IKE) and Authenticated Internet Protocol (AuthIP) keying modules. You can select the keying module in a PRISMAsync Print Server IPsec rule. |
The way how IPsec will be established is determined during the two phases of the negotiation process. Each host stores the results of the negotiations in its own Security Association (SA), that is a set of parameters that describe the upcoming IPsec communication link that is agreed on.
Phase 1
Both hosts negotiate about the protection of the initial communication. The phase 1 SA establishes a secure link over which the initial communication runs.
Phase 1 negotiations can take place in Main mode or in Aggressive mode.
|
PRISMAsync Print Server only supports Main mode. |
The phase 1 negotiations in Main mode are the following:
Encryption: Agree on what algorithms will be used during phase 1.
Authentication: Agree on what algorithms will be used during phase 1.
Security protocol: Agree on what security protocol is used.
Key exchange: Agree on what Diffie-Hellman (DH) group will be used.
Host authentication: Agree on what authentication methods will be used to authenticate the hosts.
|
Because PRISMAsync Print Server only supports ESP. PRISMAsync Print Server does not negotiate about the security protocol. |
Information that has been negotiated is stored in an IKE SA. The SA reflects an one-way communication: incoming or outgoing.
|
PRISMAsync Print Server uses the IKE SA lifetime configuration of Windows: 480 minutes. |
Phase 2
Phase 2 proceeds with the negotiation about the IPsec SA. This SA describes how the data packets are protected during the transfer between the two hosts.
Encryption: Agree on what algorithms will be used to encrypt the data packets.
Authentication: Agree on what algorithms will be used to authenticate the data packets.
Key exchange (Optionally): Agree on what Diffie-Hellman (DH) group will be used to create new symmetric keys instead of using the keys generated in phase 1.
IPsec uses the IPsec SA to check if the incoming and outgoing packets are secured according to the negotiations. IPsec treats all traffic that shares the same SA in the same way. However, SAs are restricted to a lifetime.
|
Because PRISMAsync Print Server only supports ESP, there is no negotiation about the security protocol. |
|
PRISMAsync Print Server uses the IKE SA lifetime configuration of Windows: 60 minutes. |
The encryption and authentication algorithms are used in phase 1 and phase 2.
|
PRISMAsync Print Server supports the following encryption algorithms in phase 1:
PRISMAsync Print Server supports the following encryption algorithms in phase 2:
PRISMAsync Print Server supports the following authentication algorithms in phase 1:
PRISMAsync Print Server supports the following authentication algorithms in phase 2:
The PRISMAsync encryption algorithms are not configurable individually, but as an encryption group. The group collects encryption, authentication and Diffie-Hellman algorithms that correspond with a certain strength. To configure IPsec you select the minimum level of algorithm strength that PRISMAsync Print Server accepts:
|