

Hyper Text Transfer Protocol Secure (HTTPS) is the secure version of HTTP. HTTPS is used for confidential Internet communication, for example for online transactions and social media message exchanges.
HTTPS is an Internet protocol that is established through an SSL/TLS handshake session. Web browsers such as Internet Explorer, Firefox and Chrome show the padlock icon in the address bar to indicate that a HTTPS connection is active.
SSL (Secure Sockets Layer) / TLS (Transport Layer Security) is standard technology to keep the HTTP connection secure. It uses encryption algorithms to prevent that information can be read and modified by unauthorised persons or systems. The authentication algorithms of SSL/TLS provide assured identity of the end point. TLS is an updated, more secure, version of SSL. Nowadays, TLS is the primary way to secure traffic over the Internet. Nevertheless, the term SSL is still used to describe the security technology of HTTPS sessions.
In this manual, we use SSL/TLS to refer to the SSL technology.
To establish a HTTPS connection between a client and a server, at least the Identity certificate of the server is required for authentication.
The SSL/TLS handshake session is the first step to initiate a HTTPS connection. During the SSL/TLS handshake the server and the client perform authentication and negotiation procedures. They negotiate about the TLS version, the key exchange algorithm and the algorithm to encrypt the information exchange. The set of encryption algorithms is also known as a cipher suite.
Example:
Below you find a scheme that explains the main steps of the SSL/TLS handshake between a web server and a browser.
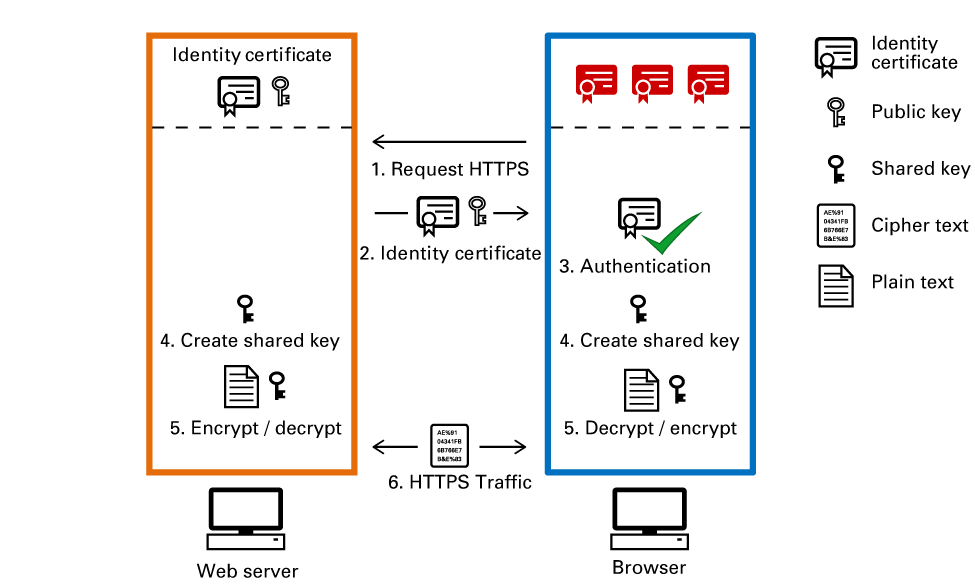 SSL/TLS handshake
SSL/TLS handshakeThe browser requests a HTTPS connection.
The web server sends a copy of its Identity certificate embedded with its public key.
The browser verifies the Identity certificate and public key.
The browser and web server agree on a shared encryption key.
The browser and web server use the same shared key to encrypt plain text into cipher text and decrypt cipher text into plain text.
To ensure the security of the connection, for each new session a new shared key is negotiated and created.