

The receiver of an Identity certificate verifies several certificate fields as part of the certificate authentication process.
 Certificate verification
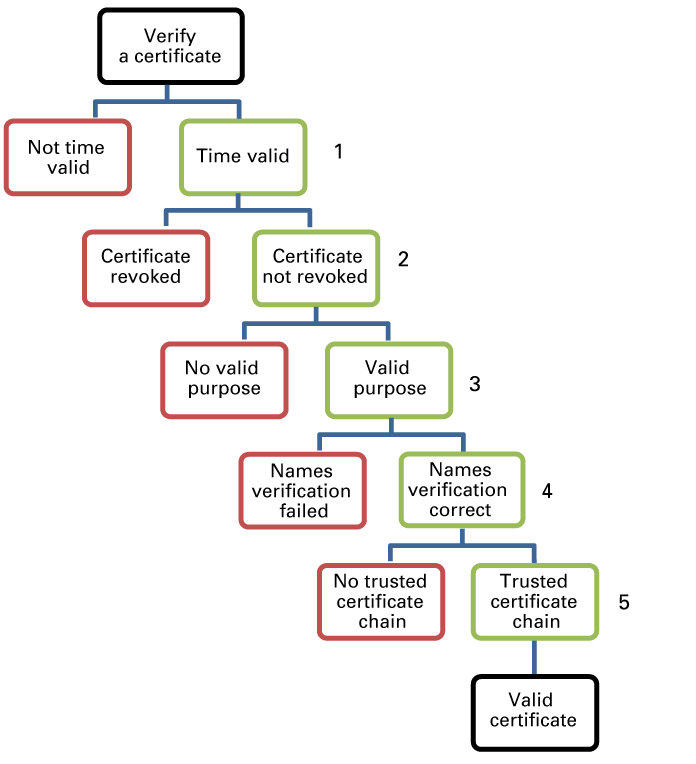
Certificate verificationAn Identify certificate is valid when it complies with a series of conditions:
The certificate is time-valid.
The certificate has not been revoked or changed.
The certificate has been issued for the purpose it is used for.
The Subject Alternative Name field of the certificate matches the Full Qualified Domain Name of the incoming connection.
The certificate can be trusted, which means that it has been verified by trusted CA certificates.
|
A PRISMAsync printer has one identity certificate to authenticate PRISMAsync Print Server. This identity certificate has been created, signed, and issued by a CA. The certificate request for the CA, also named Certificate Signing Request (CSR), is generated by the system administrator in the Settings Editor. The private key and public key that belong to the Identity certificate are also created during the CSR creation. The public key is sent with the request, but the private key is kept secure on PRISMAsync Print Server. The system administrator uploads the PRISMAsync Print Server Identity certificate in the Settings Editor. A Root CA or intermediate CA can be set up for company-internal usage. |
|
From the perspective of PRISMAsync Print Server, certificate authentication can occur on two locations.
|
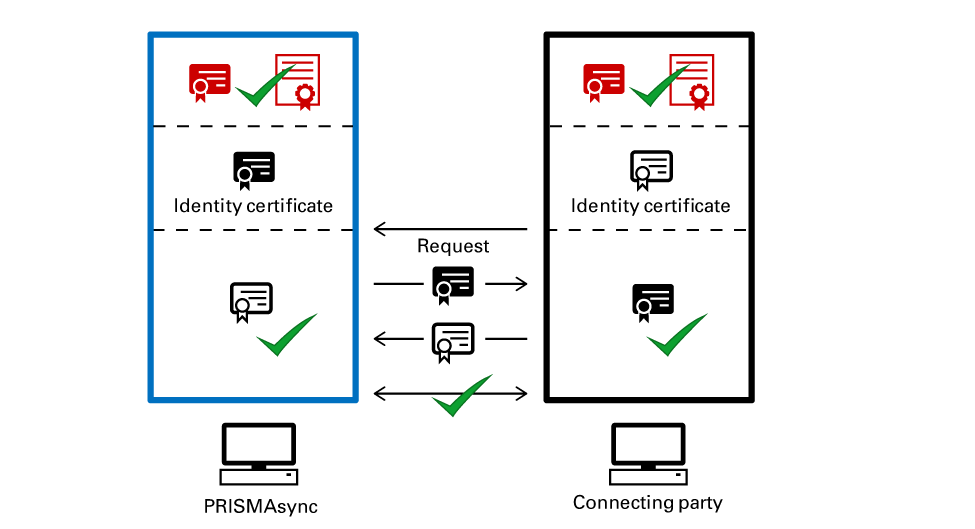
On request of another party PRISMAsync Print Server sends its Identity certificate. The PRISMAsync Print Server Identity certificate is valid for client authentication, server authentication or for both.
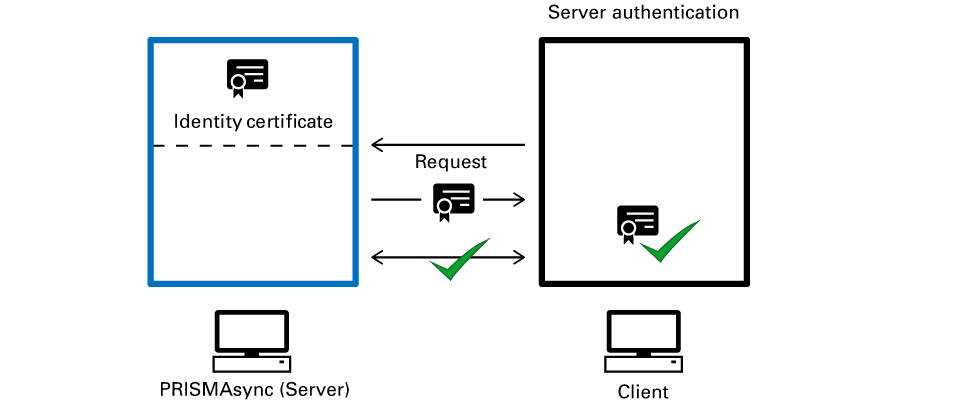
In case of Server authentication the PRISMAsync Print Server Identity certificate is authenticated when PRISMAsync Print Server acts a server. For example, when a browser wants to connect to the Settings Editor or to PRISMAsync Remote Manager via HTTPS.
 Certificate verification
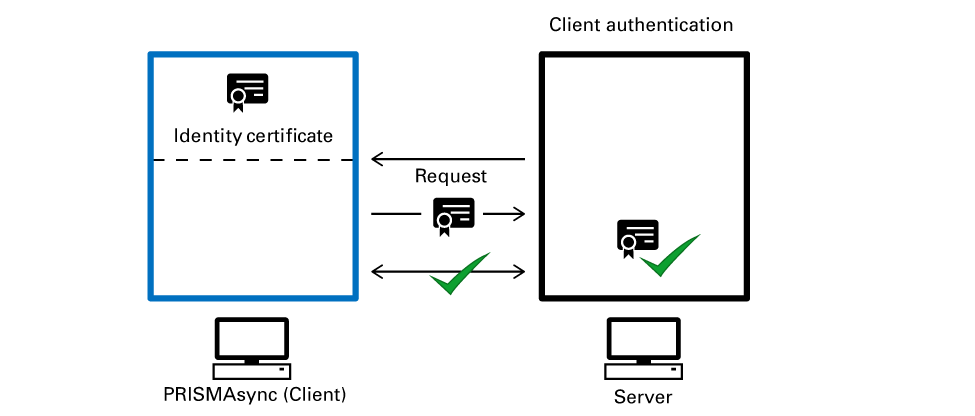
Certificate verificationIn case of Client authentication the PRISMAsync Print Server Identity certificate is authenticated when PRISMAsync Print Server acts a client. For example, when PRISMAsync Print Server wants to connect to the mail server via TLS.
 Certificate verification
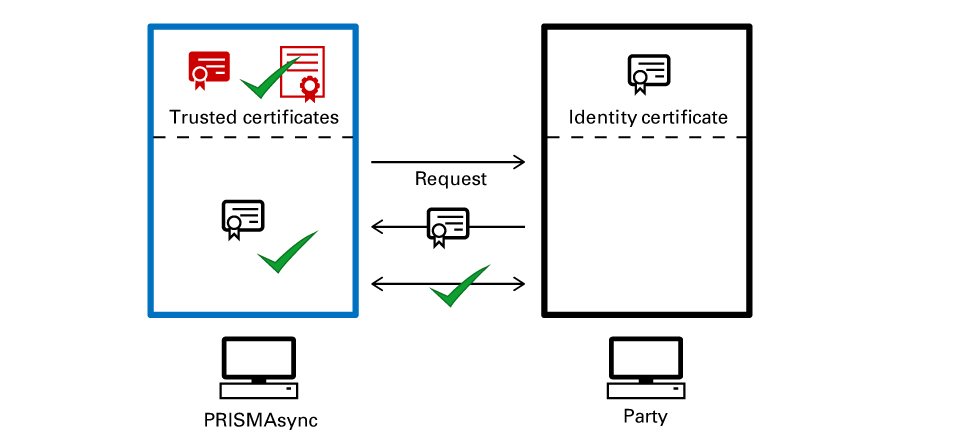
Certificate verificationPRISMAsync Print Server sends a request for authentication to another party. PRISMAsync Print Server authenticates the received identity certificate. Therefore, PRISMAsync Print Server uses the CA certificates stored in the PRISMAsync Print Server list of trusted certificates.
 Certificate verification
Certificate verificationIn case of mutual authentication both PRISMAsync Print Server and the other party exchange their Identity certificate and authenticate the Identity certificate of the other party.
|
PRISMAsync Print Server applies mutual authentication to establish a certificate-based IPsec connection. |
 Certificate verification
Certificate verificationAll CA certificates that belong to the certification chain are needed to authenticate the Identity certificate.
Example:
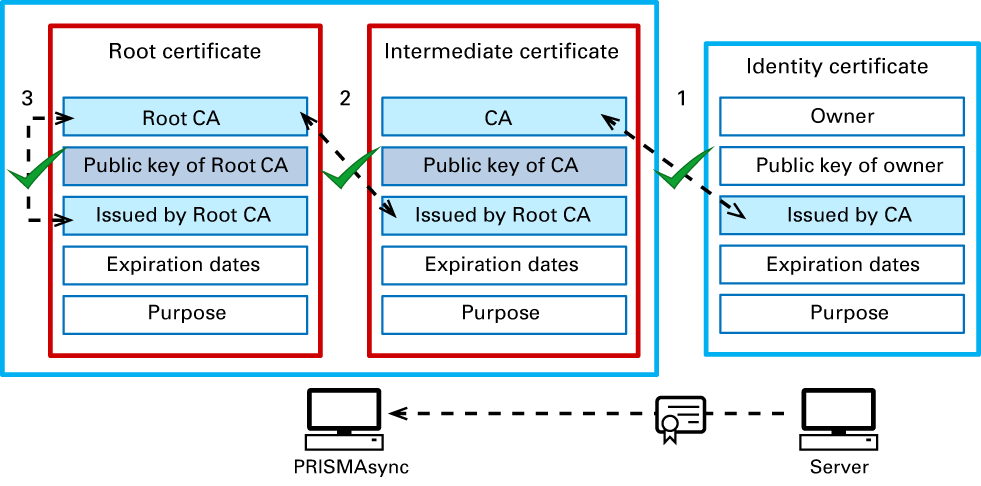
The scheme below explains how a certification chain is verified.
 Certificate verification
Certificate verificationPRISMAsync Print Server reads the issuer field of the server Identity certificate and verifies if the issuer is in the PRISMAsync Print Server list of trusted certificates. If the issuer is in the list, PRISMAsync Print Server uses the public key of the CA to verify the signature on the server Identity certificate.
The CA certificate is issued by the Root CA. Thus, this CA certificate is an Intermediate certificate. Now, PRISMAsync Print Server verifies if the Root CA is in the list. If the root CA is in the list, PRISMAsync Print Server uses the public key of the Root CA to verify the signature on CA certificate.
The Root CA certificate is issued by the Root CA itself. The signature on the Root CA certificate can be verified with the public key of the Root CA.
When all CAs prove to be trusted, the server Identity certificate is considered trusted.
|
Browsers like Chrome, Firefox, Safari and Internet Explorer have a set of pre-installed CA certificates to verify the Identity certificate of web servers like PRISMAsync Print Server. PRISMAsync Print Server stores the CA certificates of other parties in the list of trusted certificates. |